Your trusted embedded software, application & connectivity partner
Transforming your device vision into reality
Nous concevons, développons et sécurisons vos systèmes embarqués et applications

services de conception de logiciels embarqués
Du BSP, au Linux et à la maintenance sécurisée, nous garantissons des performances optimales pour vos systèmes.
Linux & Android OS, Yocto, Zephyr

services de conception d'applications & GUI
Du design UX et UI à la connectivité, à la sécurité et à l’intégration, donnez vie à vos applications.
C++, Qt, QML
Nous donnons vie
à votre produit
Nous soutenons vos équipes dans la conception, le développement et la gestion de produits innovants, du logiciel embarqué au développement d’applications.
4 pays
Certifiés ISO 27001
Fortune 500




Pourquoi choisir Witekio?
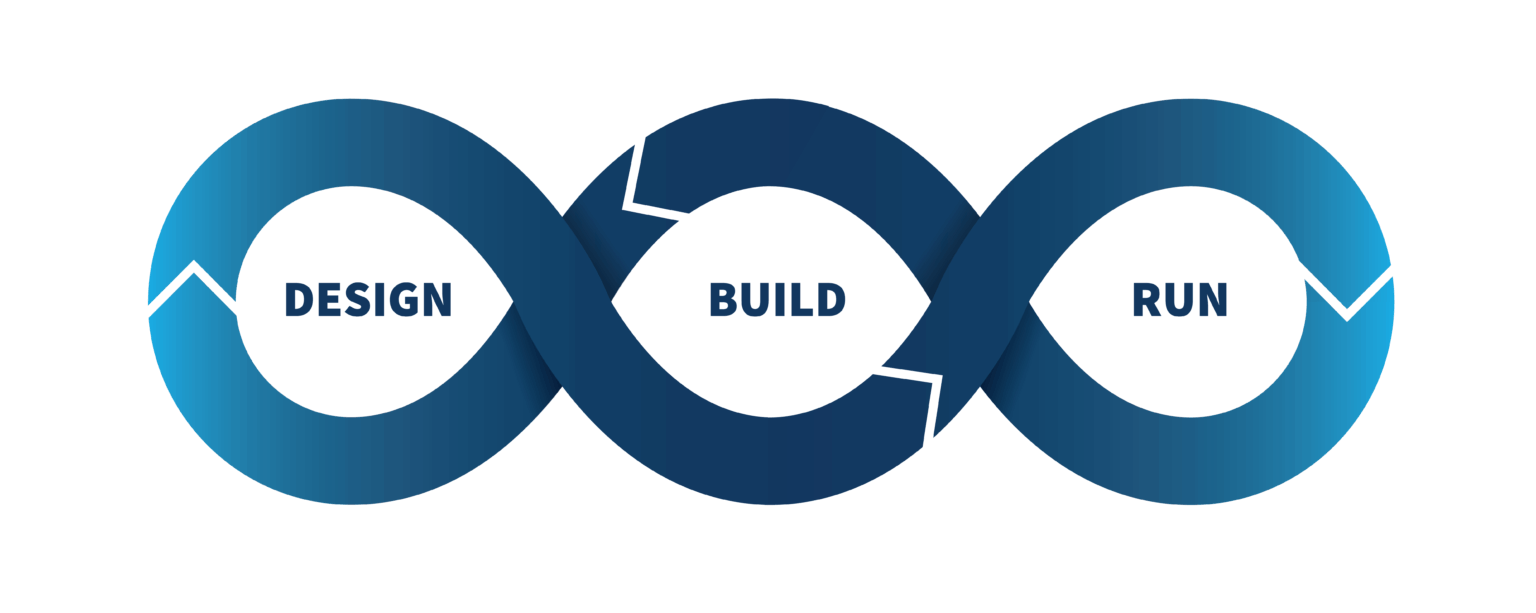
Nous donnons vie à vos produits
01. Conception
Avec plus de 170 ingénieurs logiciels, nous aidons les fabricants d’équipement à définir l’architecture adéquate pour créer des produits innovants, centrés sur l’utilisateur et hautement fonctionnels.
02. Développement
En réalisant des dizaines de projets chaque année, nos experts vous accompagnent dans le développement de systèmes sécurisés et robustes ainsi que leur optimisation.
03. Maintenance
Nous veillons à ce que vos produits fonctionnent sans accroc après leur mise sur le marché grâce à de l’amélioration continue, des mises à jour régulières et le suivi des vulnérabilités de sécurité.
Nous collaborons avec les plus grands noms de la tech























