From the Internet of Things to the Internet of Trouble: IoT security certificates
It all began with a couple of programmers that just wanted a cold Coke.
In 1982 computer science researchers at Carnegie Mellon University finally got fed up with making their way up three flights of stairs to find a vending machine that was sold out or – worse than that – buying a recently refilled soda only to find it was warm. To overcome their challenges, the programmers attached temperature switches to the machine and added connectivity that allowed anyone on the Carnegie Mellon network to know if there was Coke, and whether it was cold.
The Internet of Things (IoT) was born.
Of course, it took until 1999 for someone to put that name to these sorts of connected devices, and another ten years for these devices to outnumber actual human users of the internet. Since then, the IoT has continued to explode and today there are estimated to be more than 35 billion connected devices worldwide. Everyone from consumers looking to turn down their lights to industrial users looking to turn up their productivity have embraced the IoT, and the march of the connected device world seems unstoppable.
Or at least it did.
In the summer of 2020 alarm bells rang out regarding a major problem facing the world of IoT, one that had roots almost as far back as that Coke machine at Carnegie Mellon.
So, what could bring IoT crashing down? IoT security certificates.
IoT security certificates: The Root of the Problem
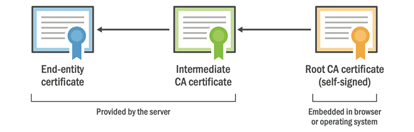
An IoT security certificate is something like a personal identity card or passport. Just as your identity card or passport assures someone that you are who you say you are, a security certificate assures that the device is what it purports to be.
With an identity card or a passport, there is a single entity issuing the document, usually a national government. With a security certificate, however, there is more than a single issuing authority and, indeed, there is more than a single IoT security certificate for each website or device.
When it comes to online security certificates there are always – at a minimum – three certificates:
- The End-Entity certificate
- The Intermediate CA certificate
- The Root CA certificate
These certificates together form what is called a chain of trust and anyone familiar with a website running HTTPS, for example, would know that their security certificate regularly needs to be updated. As of September 2020, the longest lifetime for such a certificate will be one year meaning that website owners will need to update their certificates at least annually.
Yet beyond the browsable web, all other internet-enabled devices have their own certificates, too. A sensor on a machine in a factory, a connected medical device, even connected children’s toys all have IoT security certificates that must be valid for the device to function correctly.
But while updating or replacing a certificate for an individual website or device is one thing, it’s quite another when the root certificate expires. Being core to thousands or even millions of devices, these root certificates don’t require annual updating but they do still expire.
And when they do, there’s trouble waiting.
May 30 10:48:38 2020 GMT
A couple of months back the world got a taste of what happens when a root certificate authority expires.
What is happening when your security certificate expires?
A little before lunchtime in London on 30 May, the AddTrust External CA Root expired, and the turmoil began. As a result, security researcher Scott Helme reported, IoT video streaming device Roku started losing access to some channels, global payment processor Stripe ran into issues, and competitor payment processor Spreedly was unable to process payments, too.
The underlying cause of these problems and the problems experienced by hundreds of other device makers and companies was the expiration of the root certificate authority. Without it, all of the intermediate and end-entity certificates associated with that root CA just don’t matter. Unless device manufacturers or he millions of end users update their devices, broken they will stay.
But this was just a preview.
As The Register reported, we’re approaching a point in time now where there are lots of CA Root Certificates expiring in the next few years simply because it’s been 20+ years since the encrypted web really started up and that’s the lifetime of a Root CA certificate. If manufacturers continue to churn out IoT devices and products without thinking about the implications of an about-to-expire CA root certificate, the internet of things might quickly turn to an internet of trouble.
Not All Doom and Gloom
2 steps to face this IoT security certificates issue
There is hope, though.
Indeed, the two-step solution is relatively simple to explain, if a little more complex to put into action.
Step 1 for your IoT security: pushing a firmware update to all impacted IoT devices.
Pushing updated firmware with a certificate security chain that won’t expire in the short term is essential to maintaining device uptime and continuing to meet customer expectations for reliability, robustness, and quality. For some devices with a relatively short lifecycle, a well-constructed firmware update like this will be enough to avert problems altogether, at least for the useful and supported life of the device.
Step 2: taking steps to ensure this doesn’t become a problem again in the future.
A dedicated software tool to manage the device IDs of a company’s IoT network would be ideal here. Not only would it keep track of the device, its IoT security certificate status, and highlight when that device is poised to enter a potentially unsecure period, it could also be used as part of the wider effort to manage the lifecycle of the company devices.
The first step is really the minimum that any conscientious organization is going to want to take, but it’s no panacea all on its own. The chain of trust system and the limitations on certificate validation periods mean it’s little more than a temporary stopgap.
The second step is aimed less at getting out of troublesome situations than at avoiding them altogether. With so many devices using so many certificates about to expire in the next few years, the time to start planning ahead is now.
As we approach the forty-year anniversary of the first somewhat-connected vending machine, the tens of billions of connected devices that now populate the planet are increasingly at threat from the very security that they hoped would protect. As CA Root certificates approach their expiration dates, entire IoT networks – industrial, consumer, in the factory and in the home – are at risk.
Reports note that the next major date on which a large number of root certificates will expire is 30 September 2021. With just over a year to go, the time to act is now.
IoT Security & Embedded Security
Whether an existing device with a long-life cycle in need of a security update or a new, smart or connected device that is yet to be released to the market, Witekio’s team has the knowledge and experience to help you make IoT device security a true competitive advantage.